[From the last episode: We questioned whether machinesIn our context, a machine is anything that isn't human (or living). That includes electronic equipment like computers and phones. should inevitably make decisions that humans make today.]
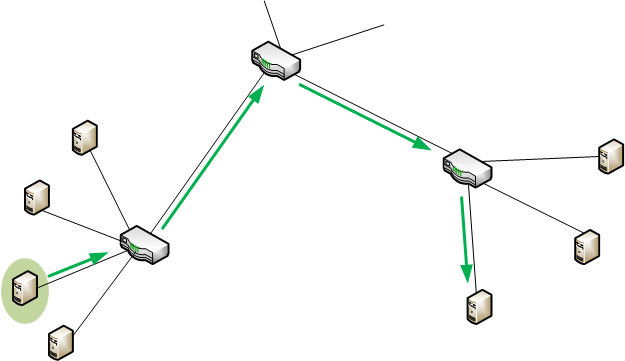
We looked before at how we send messages as packets, and how big messages may need multiple packets. We’ll now spend a few weeks looking at how we can send messages to one or more recipients. We’ll start today with the most obvious case, where one machine sends a message to one other machine. This is called unicastSending a message to one single destination. – effectively, “broadcasting” to only one destination.
This happens in the following common cases (which are just examples, since there are many more…):
- When you send an email to a single destination
- When you click on your browser to go to a website
- When one machine – say, a thermostat – sends a message to another machine – say, the heater
- When you send a private message (PM) to someone via some platformThis word can mean different things. It may mean a set of infrastructure on which someone can build an IoT device or service. Or it could be a generic piece of hardware that can be used for many different things. like Apple, Blackberry, or Facebook
This is the situation that best fits the example we used before, where sending an email is like sending an interoffice memo. Just like with a paper envelope, you have one address that is the source and one address that is the destination.
Of course, it’s not quite that simple in the details. And we need more addresses than just those two to get a message from here to there, since we have to go through many stops along the way. And, as we’ve seen, at each stop, we have to figure out where the next stop is.
Addressing a Packet
But, of course, this is where our communication stack comes into play. Up at the application layer, at the very top, our application – say, an email client – figures out where the message needs to go, and this will often look like some web address. We then go down the stackRelated to communications: A way of organizing parts of a complicated process (like communications) so that any task relies on tasks below it and feeds the tasks above it. Related to computing: A place in memory where you store “where was I?” information when you go from, say, one function into another. Before starting a new function, you store where you were in the old one so that, when the new function ends and you’re back in the old one, you can figure out where you were and continue on. to the network layer, and that’s where we translate the destination name into something more specific – usually an IP addressAn address used by the Internet Protocol (IP) to identify a machine on the network..
We’re used to IPThis can mean two things (at least):
• The Internet Protocol. Governs the addresses of sources and destinations on a network (without worrying about what’s in between). Used on Layer 3 of the stack.
• "Intellectual property." This can have lots of meanings, but, in the computer-chip world, it refers to parts of a chip design that have been built and optimized by one company, which then sells them to other companies that don’t want to design those blocks themselves. They’re not selling actual chips; they’re selling the design of a block that will be used within a chip.
addresses if for no other reason than the fact that each of our pieces of equipment needs an addressWhen referring to memory, a binary number that shows where, within some memory block, the data you want is located. If you want to read or change that data, you have to give the address so that the right data is read or changed. in order to be reachable by the internet. But there are actually two forms of IP address. The one we’re most used to is an older style, referred to as IPv4 – IP version 4. Problem is, so many things are getting IP addresses that there simply aren’t enough addresses available to give one to everyone.
We have made do for a while with tricks like giving a company one single IP address and then, inside the company’s networksA collection of items like computers, printers, phones, and other electronic items that are connected together by switches and routers. A network allows the connected devices to talk to each other electronically. The internet is an example of an extremely large network. Your home network, if you have one, is an example of a small local network., having lots of addresses for all the computers. But those addresses are valid only inside the company. They work fine when sending things within the company, but if something has to go outside on the internet, then, on the way out, the internal address has to be changed to the external address. That way, all of those internal computers don’t have to have addresses that areunique in the world; just unique within the company.
But that gets cumbersome with homes having more and more devices, for example. So there’s a new version of the address, IPv6 (yup, you guessed it: IP version 6), and it has way more addresses available – in theory, more than we’ll ever need.
So Many Addresses
IPv4 is still most common, but IPv6 is growing in use and could, presumably, completely replace IPv4 at some time. But that’s not happening anytime soon (if it ever happens at all).
Coming back to our trip down the stack, the network-layer header has to have the destination address – but, as we’ve seen, that doesn’t say how we’re going to get there. That’s the data-link layer’s job. And we’ve seen that it has its own header that gets added to the packetA group of bits being sent from one place to another. How big the group is may vary depending on what kind of packet it is. Long messages -- like an email -- will typically be broken up into many packets, each of which travels independently until it gets to the destination, where they're reassembled into the email., and that header will have the address of the next stop.
So a unicast packet will have at least two addresses in it: the network header will have the final address and the data-link header will have the next-hop address. It may also be useful to have the return address in the packet too: the address from which the message was sent. The details of what goes where within the headers varies widely depending on which protocolAn agreed way of doing something. Like a convention, except that protocols tend to be related to processes. is being used. We’re not going to get sucked down that rabbit hole; our main point here is about the concept of how we send unicast messages.
By the way, an application may be able to “fake out” messages to multiple destinations using unicast. For example, what if you send an email to three people? The most obvious way to handle that is for your email client program (or your online email system) to create a separate email for each of the three recipients. Each of those emails would then have one destination; you’d end up with three unicast messages. Is that the most efficient way to send something to multiple places? Not necessarily; that’s what we’ll look at next.

Leave a Reply