
[From the last episode: We saw how the cloudA generic phrase referring to large numbers of computers located somewhere far away and accessed over the internet. For the IoT, computing may be local, done in the same system or building, or in the cloud, with data shipped up to the cloud and then the result shipped back down. and micro-servicesSmall programs that do things that, in an earlier time, would have been done within one large program. Breaking them out into smaller programs that then act as services to other programs makes them more robust and easier to maintain. make it easier to make small, targeted, frequent software updates.]
There are a couple of other multicoreDescribes a computer chip that has more than one CPU on it. computing-related topics we need to visit before we move on from basic computing. Today’s item involves securityRefers to whether or not IoT devices or data are protected from unauthorized viewers. and processorsA computer chip that does computing work for a computer. It may do general work (like in your home computer) or it may do specialized work (like some of the processors in your smartphone)..
We talked in the past about the three places where data is vulnerable to snooping:
- At rest – that is, stored in memory somewhere, like on a hard driveA type of persistent (non-volatile) memory built from rotating platters and “read heads” that sense the data on the platters.;
- In motion – that is, as it travels through a networkA collection of items like computers, printers, phones, and other electronic items that are connected together by switches and routers. A network allows the connected devices to talk to each other electronically. The internet is an example of an extremely large network. Your home network, if you have one, is an example of a small local network.;
- In use – that is, while a processor is using it.
Our discussion today involves that last one. Processors are, of course, the things computing the data. And processors are relatively open environments – they have to be. Programmers need to be able to poke and prod to see what’s going on when a program is executing. That’s because no serious program works correctly the first time; there’s always something wrong. So programmers need to be able to figure out where the bug it – a process called, naturally, debugging.
Processors have development tools that make it easier to do that debugging. You can watch the internal results of a calculation; you can make the processor work one step at a time, looking at the results between each step; and you can investigate the value of data in registers and elsewhere. That’s all important, because that’s how you figure out what’s going wrong.
Running Sensitive Code
But what if you’re decrypting data, and you’re doing it in the processor? A brute-force approach would mean that you fetch the encryptedEncryption refers to encoding and decoding (or encrypting and decrypting) data so that it can't be read unless you have the right key. It's critical for good security. data from memory, and then you fetch a keyA number used to encrypt (or encode) information so that no one can read it. Keys are used when encoding and decoding. You shouldn't have to mess with keys yourself. from somewhere, and, with the key, you decrypt the data. With a debugging tool, you could literally look to see what the key was. That’s about as insecure as you can get.
Instead, we saw that hardware roots of trustA chip of some sort that stores security artifacts like keys and certificates. It can perform the security operations itself so that those artifacts never have to (and can never) leave the chip. (HRoTs) can help, since they do the cryptographic work in a way that can’t be snooped. But, if you look at the entire range of things that might be sensitive – beyond this one obvious example – there is a whole family of security-related stuff that needs doing. And if you simply run that as software on the processor, you’re doing it where everyone who wants to can see.
What we really need is someplace more private where we can execute the sensitive stuff. Doing so ultimately relies on trust, in the way that so many security-related things (like certificates) do. Can you set up a trusted environment for running sensitive stuff?
The answer is yes, and it takes us back to multicore processors. Only now, we’re not talking about just another coreThis can have more than one meaning. When discussing networks, the core is the heart of the network where much of the traffic (or at least that part that has to go a long ways to its destination) moves. This is in contrast to the edge -- the outer part of the network where devices like computers and printers get connected. When discussing computers, you can think of it as the same as a CPU. to help with the processing load; we’re talking about a specific, special core with special privileges and even special instructions that work only with that core. It’s “walled off” from the rest of the chip so that you don’t get direct visibility into it.
A Trusted Place for Sensitive Code
In addition, the operating systemSoftware – or firmware – that handles the low-level aspects of a computer or IoT device. It gets direct access to all the resources. Software asks the OS for access to those resources. can have some trusted walled-off functions – far more than the HRoT can handle. Data and operations are better protected – what goes on here is effectively isolated from the other software running on the other cores. Together, protecting the hardwareIn this context, "hardware" refers to functions in an IoT device that are built into a silicon chip or some other dedicated component. It's distinct from "software," which refers to instructions running on a processor. core and the software it runs, you’ve got what’s called a Trusted Execution EnvironmentA separate area inside a processor where trusted software can run, with access to all resources. Software running outside that area has to access resources through the trusted area; it can’t do so directly., or TEE.
If you’re writing a program and need something that involves secure data, and you don’t want to do it out in the open, then how do you do it if you can’t directly access the secure core? The operating system helps with that. It walls off the secure stuff, but it offers up a way to have the trusted secure area perform some critical functions – you just can’t see or control them. You ask it to do something, and it gives you the answer without you being able to see how it did that.
The following figure illustrates this. It shows the communication between the open and trusted areas as happening through the OS. Depending on the specifics, it could happen there, or in some lower-level firmwareSoftware that is stored on a device itself. Regular computers have very little firmware, since software mostly comes from a hard drive or some other storage. But on IoT devices, much of the software may be firmware.; there could also be some hardware connections.
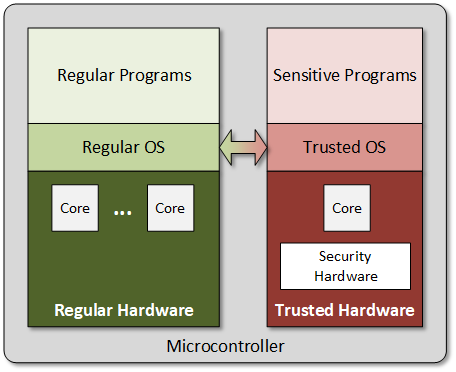
One common example of this comes from Arm (now owned by SoftBank). They make processors that you could find in a huge number of chipsAn electronic device made on a piece of silicon. These days, it could also involve a mechanical chip, but, to the outside world, everything looks electronic. The chip is usually in some kind of package; that package might contain multiple chips. "Integrated circuit," and "IC" mean the same thing, but refer only to electronic chips, not mechanical chips. and applications. They’re particularly common in devices with a specific purpose (as opposed to general-purpose laptops and such). They have branded their version of this as TrustZone.
This arrangement tends to be more favorable for larger microcontrollers, where the price and amount of hardware can be tolerated. It’s harder for very small processors for very inexpensive devices. The truth is, we all want security, but… often, we don’t necessarily want to pay for it.

Leave a Reply