
[From the last episode: We saw how the UK was approaching the need for better IoTThe Internet of Things. A broad term covering many different applications where "things" are interconnected through the internet. securityRefers to whether or not IoT devices or data are protected from unauthorized viewers..]
We’ve looked at some important security concepts, and we’ve looked at some of the different ways in which security can be implemented – and even thwarted. But you might think that secure communications are somewhat separate from the other communications stuff we looked at earlier, like the seven-layer OSI stack.
In fact, that’s not the case. Security plays in the stackRelated to communications: A way of organizing parts of a complicated process (like communications) so that any task relies on tasks below it and feeds the tasks above it. Related to computing: A place in memory where you store “where was I?” information when you go from, say, one function into another. Before starting a new function, you store where you were in the old one so that, when the new function ends and you’re back in the old one, you can figure out where you were and continue on. just like so many other things do. And, in fact, there are different elements or options for security within multiple layers of the stack. But these aren’t all redundant versions of security; they each have an intended role, so there’s less overlap than you might think.
Network Review
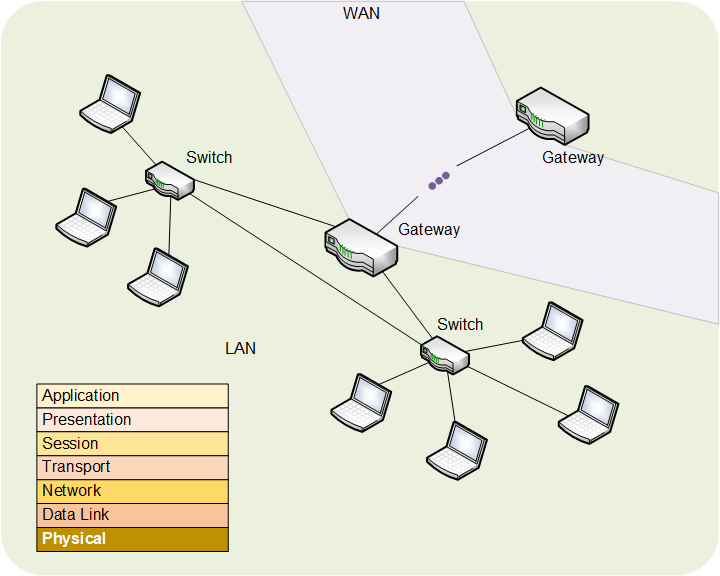
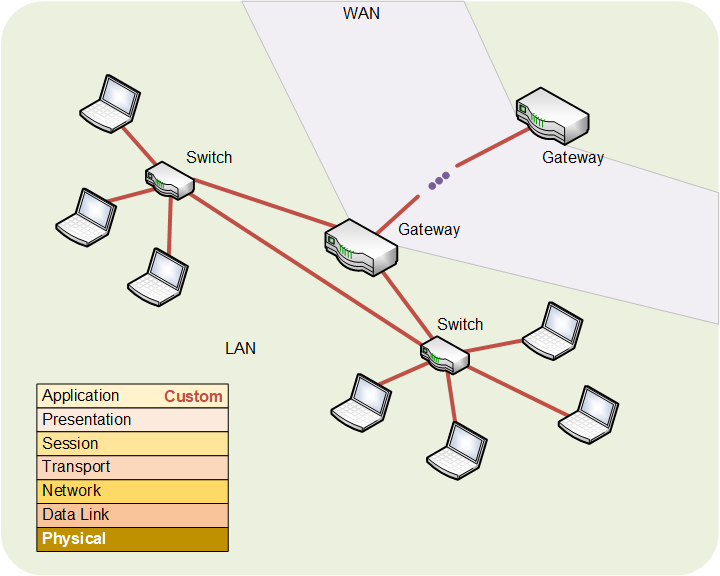
Before we talk about the different security protocolsAn agreed way of doing something. Like a convention, except that protocols tend to be related to processes., let’s review the OSI stack along with some basic networksA collection of items like computers, printers, phones, and other electronic items that are connected together by switches and routers. A network allows the connected devices to talk to each other electronically. The internet is an example of an extremely large network. Your home network, if you have one, is an example of a small local network.. In the image below, you see laptops (two groups) connected to switchesA switch helps direct network traffic to the right destination. At a high level, it's very similar to a router. Technically, switches are used to create local subnetworks; routers connect subnetworks together., which are connected to each other. Together, this makes a local-area networkA data-link-layer security protocol, largely used with Ethernet. This protects data within a LAN only. It’s normally administered by IT professionals. Not likely to be used within IoT devices., or LAN. That’s the basic network, for example, in your office or your home. In all of these drawings, we’re showing computers, but they could just as well be IoT devices, so the concepts are equivalent.
The switches connect to a gateway, which takes trafficRefers to any kind of electronic message -- email, web request, streaming video, or anything else -- that travels over a network. out of the LAN onto the wide-area networkWide-area network. This is a broad description of the core networks that connect different LANs together around the world. When traffic leaves a building, it usually goes through a gateway out onto the WAN before returning elsewhere through a different gateway into a different LAN. You could think of this as the internet., or WAN. That’s how messages get out of your building and arrive at the gateway of some other building. There are lots of ways they could travel on the WAN, but we don’t care about that for right now. For our purposes, it’s more or less equivalent to the internet (although that’s not technically true).
Finally, you see the OSI stack, running from physical layer at the bottom all the way to the application layer. In each of the drawings that follow this one, I’ll show the secured connectionsThis refers to some kind of electrical connection. It might be through a network cable, a cable connection, a wireless connection, or a phone - just to name some options. The connection might be to the internet or to some other local device. in red, and I’ll show the protocol name in the stack.
Data-Link Security: MACsec
Let’s move up the stack. The first level that has security is the data link layer, of which EthernetA very common Layer 1 and 2 standard for wired network connections. is the most well-known protocol. MACsecA data-link-layer security protocol, largely used with Ethernet. This protects data within a LAN only. It’s normally administered by IT professionals. Not likely to be used within home IoT devices. involves numerous keysA number used to encrypt (or encode) information so that no one can read it. Keys are used when encoding and decoding. You shouldn't have to mess with keys yourself. to protect all kinds of things. It’s for when you need to the local traffic to be secure. What we show below looks like an office setup, but it could also be your home or even a data centerA collection of computers that are interconnected so that they can share and distribute work. For our purposes, it’s the same as a computer farm, but the focus is on its application for processing data.. The point is that it’s local.
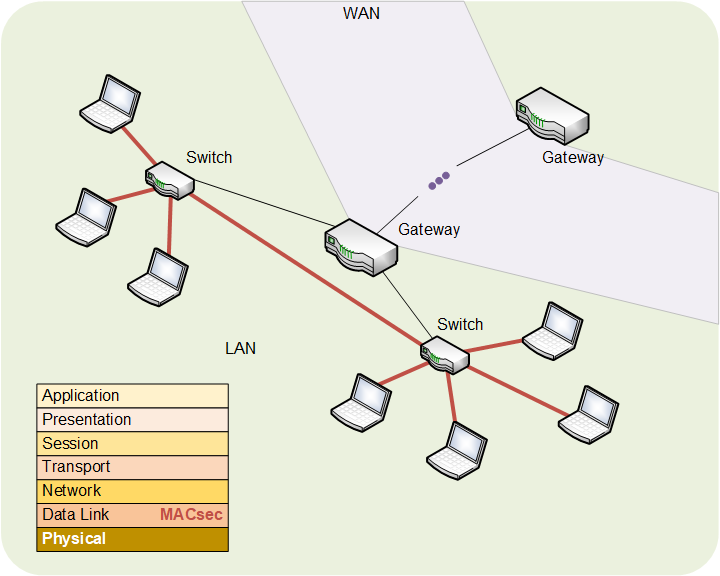
MACsec is managed by IT professionals; individual computer (or other device) users (like you) wouldn’t normally be involved. Specifically with respect to the IoT, it’s unlikely you’d be using MACsec in your home, so smart-home devices wouldn’t likely implement MACsec. Enterprise or industrial IoT installations, on the other hand, might use MACsec if traffic must be protected locally.
Bottom line: you’re not likely to use this.
Network security: IPsec
Moving up to the network layer, we can use IPsecA network-layer security protocol. Largely used between gateways for traffic traveling between (but not within) LANs. Not likely to be used within IoT devices. to protect individual IPThis can mean two things (at least):
• The Internet Protocol. Governs the addresses of sources and destinations on a network (without worrying about what’s in between). Used on Layer 3 of the stack.
• "Intellectual property." This can have lots of meanings, but, in the computer-chip world, it refers to parts of a chip design that have been built and optimized by one company, which then sells them to other companies that don’t want to design those blocks themselves. They’re not selling actual chips; they’re selling the design of a block that will be used within a chip.
packets. Because those packets have parts that get inspected and changed with each hop through the network, not all parts of the packetA group of bits being sent from one place to another. How big the group is may vary depending on what kind of packet it is. Long messages -- like an email -- will typically be broken up into many packets, each of which travels independently until it gets to the destination, where they're reassembled into the email. are encrypted. But the major portion is.
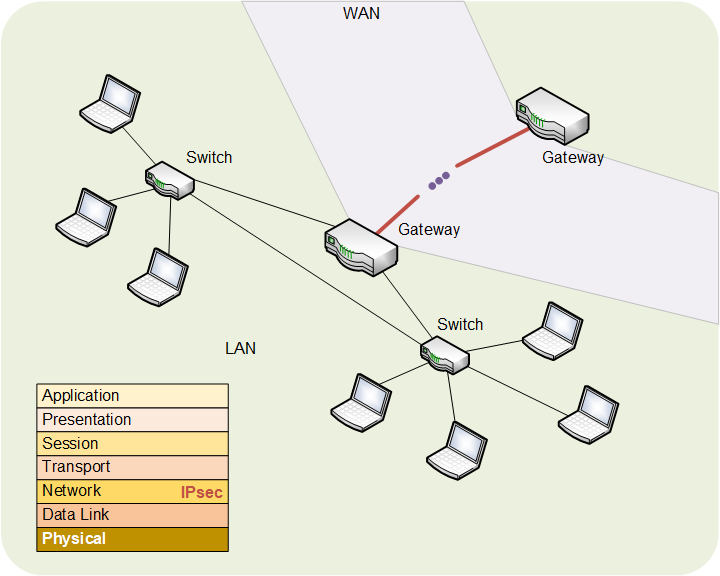
IPsec is normally implemented in gatewaysA piece of electronic network equipment that takes a local network and gives it access to the internet. Your cable modem, for instance, might act as a gateway., encrypting packets before they leave the gateway and go out onto the WAN. When received by a gateway at the other end, the IPsec stuff is first checked to make sure there wasn’t a problem en route. Assuming everything is ok, the IPsec stuff is removed as the packets travel around the LAN.
This means that the actual devices at the edgeThis term is slightly confusing because, in different contexts, in means slightly different things. In general, when talking about networks, it refers to that part of the network where devices (computers, printers, etc.) are connected. That's in contrast to the core, which is the middle of the network where lots of traffic gets moved around. of the networks – laptops, IoT devices, etc. – won’t likely implement IPsec. Only the gateways will.
Bottom line: you’re not likely to use this.
Transport Security
The fourth layer is where the more familiar security stuff happens. We saw quite a while ago that there are two main protocols here: TCPTransmission Control Protocol. A more reliable way to set up connections that might have two-way traffic or need better guarantees that messages get delivered. Used on Layer 4 of the stack. and UDPUser Datagram Protocol. A “best effort” (i.e., no guarantees) way to get a message from one place to another. Used on Layer 4 of the stack.. There are two security protocols that go along with these: if you use TCP, then there’s TLSTransport Layer Security. A very common internet security protocol. You can think of it as an updated version of SSL, although both are still used. Used with TCP on Layer 4 of the stack. (which hosts the authentication process we talked about before). If you use UDP, then there’s DTLSDatagram transport-layer security. This is a security protocol analogous to TLS. TLS is used with TCP; DTLS is used with UDP (which sends so-called datagrams). Some version of this or TLS should be in IoT devices. (for datagram TLS).
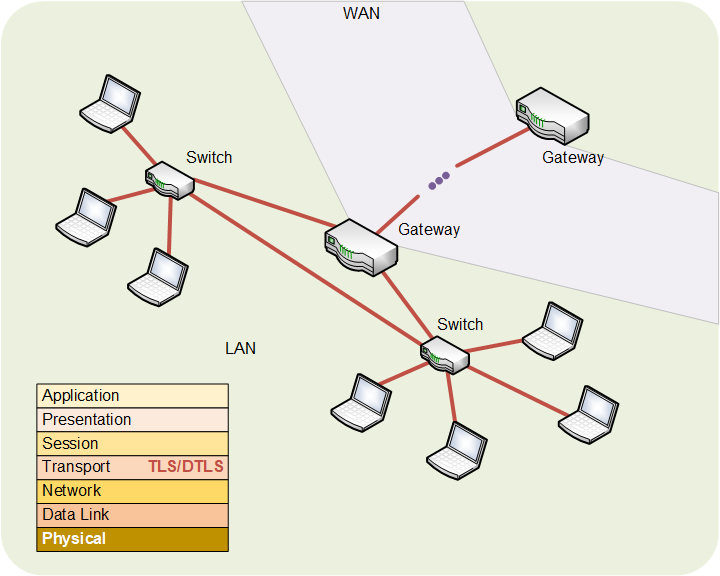
The TLS (or DTLS) stuff travels with a packet from when it leaves one device until it arrives at the final device, whether on the LAN or WAN.
Bottom line: some form of this should be operating in your IoT devices.
Application-Level Security
Finally, if you’re designing an IoT device and you want the most security, you’d put in your own version right up at the application layer. Yeah, why do that, since you could simply use TLS? Well, if someone cracks TLS (or whatever) and exposes the payloadThe main contents of a message. Using an analogy, when you receive a letter in the mail, the letter itself is the payload; the envelope is merely a carrier., then, if you’ve got your own security, the payload will be unreadable (unless someone cracks your security).
You might think this is the same as using TLS, since the custom security drawing above and the TLS/DTLS one above that have the same red lines. But here’s the difference. Remember the notion about payloads starting in the app layer and moving down (conceptually) as they prepare for travel? Well, if you use TLS, then your data is unprotected even within your own systemThis is a very generic term for any collection of components that, all together, can do something. Systems can be built from subsystems. Examples are your cell phone; your computer; the radio in your car; anything that seems like a "whole." until it gets to the transport layer, where it finally gets encrypted.
With app-layer security, the application itself encrypts the payload before sending it down the stack. And an application writer can use any form of encryptionEncryption refers to encoding and decoding (or encrypting and decrypting) data so that it can't be read unless you have the right key. It's critical for good security. they want (hopefully one that’s hard to crack). That’s what’s different, for example, about the WhatsApp and Signal phone apps: the messages are encrypted before they leave the app, and they’re not decrypted until they get to the destination app.
With forms of security in the lower layers, the stopover points have the ability to do some inspection of the packets – and possibly even decrypt them. This creates more opportunity for trying to snoop the contents. With app-level security, no one along the way can snoop. Not even the government. For this reason, app-level security is often referred to as end-to-end security.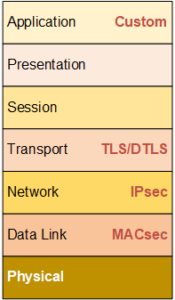
For IoT devices, if there’s truly delicate data, then app-level security might be appropriate. But it adds softwareIn this context, "software" refers to functions in an IoT device that are implemented by running instructions through some kind of processor. It's distinct from "hardware," where functions are built into a silicon chip or some other component., which means more memory, and which might mean a beefier processorA computer chip that does computing work for a computer. It may do general work (like in your home computer) or it may do specialized work (like some of the processors in your smartphone)., all of which costs money. Home IoT devices have to be reasonably priced, and so they’re unlikely to include this level of security.
Bottom line: TLS or DTLS are the most likely forms of security in your home IoT devices. Which is why we focused on it in our earlier security discussions.

Leave a Reply