
[From the last episode: We saw how we can build a packetA group of bits being sent from one place to another. How big the group is may vary depending on what kind of packet it is. Long messages -- like an email -- will typically be broken up into many packets, each of which travels independently until it gets to the destination, where they're reassembled into the email. out of a simple message.]
Now that we’ve built the basics of a packet, let’s send that packet on its way to see how it changes as it goes. Because we’ve started at the application layer of our communications stack, we now start moving down the stackRelated to communications: A way of organizing parts of a complicated process (like communications) so that any task relies on tasks below it and feeds the tasks above it. Related to computing: A place in memory where you store “where was I?” information when you go from, say, one function into another. Before starting a new function, you store where you were in the old one so that, when the new function ends and you’re back in the old one, you can figure out where you were and continue on. so that we can physically send the message out.
- There’s not much going on at the presentation and session layers for this kind of message, so nothing may happen there. Then, moving down another layer, you get to transport.
- At the transport layer, you may tack on something to ensure that the message is received correctly. You could do that with scrambling codes, for instance, where you scramble up the payloadThe main contents of a message. Using an analogy, when you receive a letter in the mail, the letter itself is the payload; the envelope is merely a carrier. and attach that to the end of the payload. Then, on the receiving end, you recover the payload and re-scramble it. The newly scrambled version should match the scrambled bitThe smallest unit of information. It is a shortened form of "binary digit." Since it's binary, it can have only two values -- typically 0 and 1. that you sent in the packet. If not, then the message got corrupted and should be resent. This is but one example of what could happen at this layer. From here we go down to the next layer below.
- At the networkA collection of items like computers, printers, phones, and other electronic items that are connected together by switches and routers. A network allows the connected devices to talk to each other electronically. The internet is an example of an extremely large network. Your home network, if you have one, is an example of a small local network. layer, you figure out the final addressWhen referring to memory, a binary number that shows where, within some memory block, the data you want is located. If you want to read or change that data, you have to give the address so that the right data is read or changed. of the ultimate destination. We saw last week, for example, that the ARP protocolAn agreed way of doing something. Like a convention, except that protocols tend to be related to processes. can help fetch the IPThis can mean two things (at least):
• The Internet Protocol. Governs the addresses of sources and destinations on a network (without worrying about what’s in between). Used on Layer 3 of the stack.
• "Intellectual property." This can have lots of meanings, but, in the computer-chip world, it refers to parts of a chip design that have been built and optimized by one company, which then sells them to other companies that don’t want to design those blocks themselves. They’re not selling actual chips; they’re selling the design of a block that will be used within a chip.
address of the intended destination. Note, however, that this says nothing about the route the packet will take to get from here to there. - At the data link layer, we worry about the next hop. What’s the first stop along the way to the destination? Computers keep tables that help point the way. Just like with ARP, if they don’t have the right table entry yet, they can inquire for help from other routersAn electronic box that helps steer data on a network. For instance, you may have one in your home connecting your phone and computer and other devices to each other and to the internet. The data itself has information about where it's being sent; the router uses that information to send it in the right direction. At a really basic level, you can think of a router and a switch as being the same thing. If you want to get more technical, a switch creates a local subnetwork, and the router connects multiple subnetworks (or multiple networks). that do have that info. So the address of the next stop is then added to the packet. When it reaches the next stop , we repeat this process, stripping off the old next-hop address and replacing it with a new address. This happens over and over until the packet finally arrives at its final stop.
- At the physical layer, we send the packet out onto a wire or into the air.
Wrap it Up
At most of these steps, we add something new to the packet – like an address. We add much of that in front of the payload, and there we refer to it as a header. Each layer may add its own headers. We can call anything added at the end a footer or a signature. Again, you might have multiple signatures.
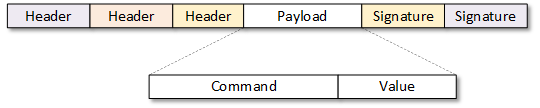
So what happens when the packet arrives at a new machineIn our context, a machine is anything that isn't human (or living). That includes electronic equipment like computers and phones.? Note that the new machine might be the final destination, or it might be a stop along the way.
- A received packet comes in the bottom layer and then moves up to the data link layer. This is where the address swap happens if this isn’t the final address.
- If it is the final address, then we remove the data link header and send the packet to the network layer.
- At the network layer, we can remove the header with the final address portion of the packet before sending the remainder of the packet up one more layer.
- At the transport layer, we might perform the various transport management things – like checking to make sure the message wasn’t corrupted. Then we can strip off all of that management stuff (headers and/or signatures), and we’re left with the original payload at the application layer.
It’s very much like that interoffice memo example we went through when introducing stacks. A letter goes into an envelope with an address; the envelope might end up combined with other letters in a bin or box with the address of the next transfer location; etc. And when the letter is received, the outer boxes and envelopes are removed each step of the way, just like removing the headers and signatures. I’d encourage you to review that post if this isn’t clear yet.
Watching a Packet Move
I’ve tried to illustrate this in the following video. For the sake of brevity, I don’t show intermediate stops; just the starting and ending stacks. It assumes a machine command, so there’s no presentation- or session-layer stuff.

Leave a Reply